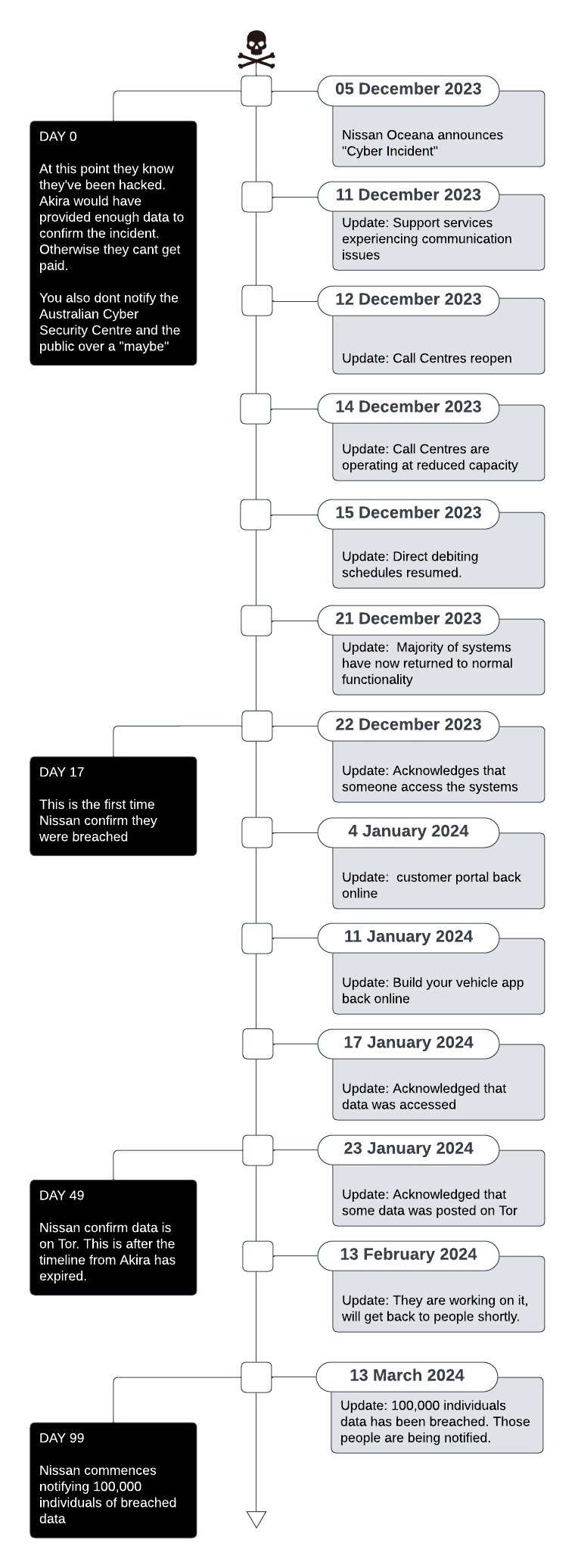
This one started last year, but is still in the final stages of being dealt with. On the 5th of December 2023, the ransomware group Akira hacked one or more internal systems at Nissan Oceana and copied out 100+GB of data.
Since then, Nissan has been providing updates on its website at: www.nissan.com.au.
There are a few interesting aspects of this breach that stand out, so this post will be a little longer than previous ones. My appologies to those with TikTok attention spans.
This is also the first time I’ve seen a company provide a running timeline of their “Cyber Incident” and remediation efforts. As always, the comms has been thoroughly bleached by the legal / PR team.
Here’s the timeline of events so far:
Impact
We now know the list of affected individuals includes some of Nissan's customers (including customers of our Mitsubishi, Renault, Skyline, Infiniti, LDV and RAM branded finance businesses), dealers, and some current and former employees.
Nissan Oceana
The type of information involved will be different for each person. Current estimates are that up to 10% of individuals have had some form of government identification compromised. The data set includes approximately 4,000 Medicare cards, 7,500 driver’s licenses, 220 passports and 1,300 tax file numbers.
The remaining 90% of individuals being notified have had some other form of personal information impacted; including copies of loan-related transaction statements for loan accounts, employment or salary information or general information such as dates of birth.Nissan Oceana
Details
A lot happened with this breach, including Nissan taking multiple production systems offline for an extended period. The last system restored (Nissan Financial Services Customer Portal) was not online until the 4 of January 2024.
That’s a 30-day outage of core systems. A pretty big clusterfuck by anyone’s standards. I’m shocked the infra team wasn’t eviscerated for this once things were back online.
No specific technologies have been mentioned beyond these references.
“accessed some of the company’s network systems in Australia and New Zealand.” and “accessed some of Nissan’s local systems in Australia and New Zealand”.
Lets look at some obvious assumtions we can make about the breach.
Data stolen/locked
There’s no way this was a basic data for cash ransomware attack. You dont take your production systems offline for that. So we can only assume multiple servers were crypto locked and inacessible.
Which brings up the obvious questions of:
Does Nissan even have a DR plan?
Shit happens, and eventually, you’re going to get hit with a destructive outage. Which is why we have Disaster Recovery plans.
You’ve all got one. It’s that Word doc/PDF stored on the file server, written by some consultant about 3 years ago. Of course, it was a load of gibberish then, and now it’s out-of-date gibberish. But it keeps the Risk Manager off your back and lowers your cyber insurance premiums.
Very obviously, Nissan hasn’t brushed the dust off theirs recently.
Regardless of how Akira breached and locked Nissan’s data, a 30-day window to recover from backups is a clusterfuck.
DevSecOps what?
Nissan states that the affected systems were internal ones, so it was likely IT servers. The sort of fragile snowflakes that every large org has. If they were really unlucky, it could even have been their ERP.
These are the systems that have been around forever, never get rebuilt, and are patched by hand after a full backup. These applications are always a manual build process, and the concept of DevOps never enters the picture. If you talk to the infra team about “Infrastructure as Code” they get a twitchy eye and reach for the nearest SCSI drive to beat you with.
Which means building them from scratch is slow, and restoring them from tape is even slower.
Hence, 30 days.
All your eggs in one basket
Nissan lost multiple systems ranging from email to the customer support centre. These are disparate services and are very unlikely to be on the same servers (though I’ve seen it done). Which means Akira gained access to multiple core systems.
These are servers well inside the DMZ.
It tells us Akira either had escalated permissions across multiple servers (most likely) or were able to deploy malware that spread from server to server.
Either way, there was clearly limited segregation of these systems at the network level.
Too damn slow
Everything about this has been slow, and the reasons (excuses) given are garbage. From beginning to end, this has taken 99 days so far. Even now, the 100,000 individuals still haven’t been notified of what data was breached.
That’s over two months, thatgovernment ID’s and banking records have been in the wild and available for exploitation.
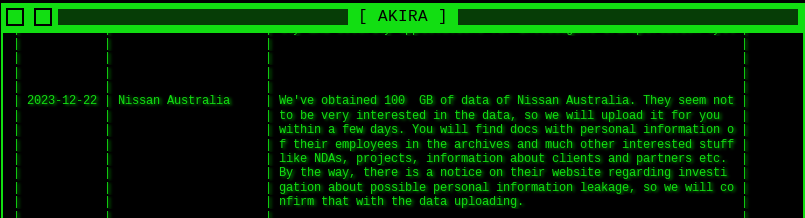
Anyone who works in this space knows it doesn’t take 99 days to work out what data was stolen. For starters, the ransomware team is more than happy to tell you, so that they can maximise the fear and get paid.
Even if they were only working 9-5, it doesn’t take that long to go through the logs. I’m sure they have centralised logging, right? Right?
Logs that aggregate back to a service like Splunk or SumoLogic and allow for rapid searching?
One would think a company of Nissan’s size even had a SIEM solution in place?
It just doesn’t take this long to identify what data was stolen, especially when the thief tells you what they stole.
Communication
I’ll give the Legal/PR team at Nissan credit, the notifications have been artfully crafted. Professional, confident, hits the key legal obligations and reenforces that they are working very hard.
I mean, this is a company suffering a major outage of its internal systems and 5 days in, says, “We are aware that customers … are having difficulties contacting us”.
Don’t play poker with these people.
I was surprised at the focus of the initial messaging. The first 5 updates are about them bringing their systems back online, and it’s not until Dec 22nd that they admit someone illegally accessed their data.
They managed to say “Cyber” 28 times and only use the word “Breach” twice. And even then only in the last statement, because at that point its an official OAIC breach. Zero use of scary words like “Hack”.
They met their OAIC commitments on day one, by notifying the relevant departments of a suspected breach. From there they don’t have to do anything unless they identify the breach has a risk to causing individual’s “serious harm”. They preempt this in the 17 of January update by saying “Where we identify customer data has been accessed in a manner which gives rise to a risk of serious harm”.
Until they acknowledge that, they are still in the assessment phase and don’t to inform those who’s data is breached. Though the OAIC does encourage early communication.
Overall, this breach hasnt goten a lot of attention, which is surprising considering the size of the company. They barely registered as a blip (blue spike) in the general breach chatter.
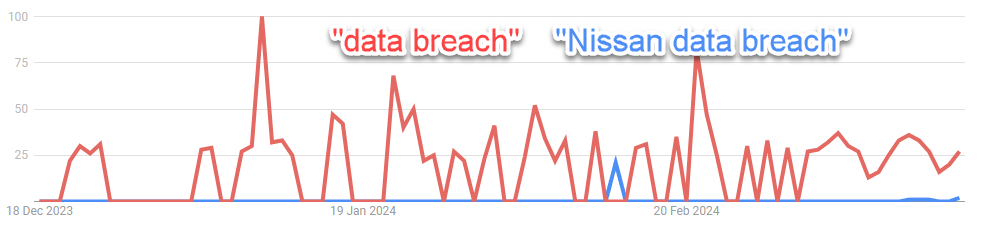
That might change now that they have announced the number of people affected.
Opinion
PII Data is radioactive
As I am documenting these breaches, the single biggest issue I see is the storage of Personally Identifiable Information (PII) data.
Companies are persistently storing customer/employee personal ID/data in ways that are not secure.
Conceptually, this is really basic stuff, but the implementation is complex and expensive. Which is why so many companies fuck it up. It’s not that they cant or dont know how. They just dont want to spend the budget on it.
There is mountains of guidance on the topic, but my go to advice is:
- DONT STORE THE DATA. Use an ID verification service
- If you must store it, store it on a dedicated system. Something issolated and only accessible via tightly controlled interfaces
- Never store images of ID’s on a file storage service such as file servers, Google Drive, Dropbox etc. Just dont do it.
There is no accountability
Even a breach, like this one, has minimal impact on the business and the staff. We are yet to see how the Nissan breach plays out, but I would be very surprised if they are penalised by a government body in Australia.
They will have had some loss associated with the outage and remediating the issue, but that’s all. Even this will be offset by insurance.
The remediation work will actually be a net return for them, as they will have hardened their systems. So it’s not like they just set the money on fire.
So 100,000 people are impacted and Nissan walks away with upgraded PII storage, some audits and updated practices.
One of the key issues is that companies don’t have to reveal how they got hacked and what mistakes they made. 10,000 people just had their government issued ID’s stolen, but nobody at Nissan has to explain to the public how this happened.
- Did they fail to patch something?
- Was the solution inherently unsecure?
- Who authorised the breached IT solution?
- Who knew this system was poorly secured and didn’t act?
- Was the CISO/CTO/CIO aware of security issues?
Did anyone even get fired for this clusterfuck?
Companies should be forced to identify HOW they fucked up, WHY they fucked up and who is looking on seek for a new job because of it.
Of course the OAIC and other regulatory bodies arent going to enforce that kind of transparency. That would expose companies to civil suits when they get breached. The OAIC like everyone else in the tech industry knows that companies are rife with garbage IT security solutions and cant afford to have them exposed.
It’s far more politically expedient to make 10,000 people get new drivers licences, then get lobbied or risk campaign donations.