The nature of the beast
With the amount of data breaches in the news of late, many people keep asking why companies are not doing more to secure customer data. The public tends to assume that companies have:
- People trained to look after cybersecurity
- An obligation to secure customer data
In reality, the role of a CISO is to be the CEO’s fixer and exists to ensure:
- That the company continues to operate at all times
- That the business is not at risk of unmanageable legal repercussions
- That the business can pass regulatory compliance audits
- Identify any relevant legal obligations related to IT security
- Advise executive team on risks
- Mitigate those risks
The CISO doesn't have to secure anything
When we talk about cybersecurity obligations of an organisation and the CISO, we are talking about civil and criminal legal obligations. If it’s not written in law, it’s entirely optional.
At no point does a CISO (or anyone in the IT/security team) need to actually secure anything, what they have to do is meet their legal obligations. Most people have a very distorted idea of what a given company is obligated to do to protect customer data (or any other IT system). The government talks highly of its regulatory frameworks, and companies like to shout about how compliant they are (when it suits them). The reality is though, those legal obligations are:
- Incredibly limited
- Trivial to sidestep
- Cary no meaningful repercussions
If you actually read it though, it is very obvious that the legislation is incredibly vague and provides enormous scope to be circumvented. This applies to any other laws and frameworks relevant to data protection, from PCI DSS to ISO27001.
I've got to be taking the piss right?
I know what you’re thinking. “David, you’re being a cynical asshole and just putting a negative spin on the well-intentioned efforts of organisations”. And you’re both right and wrong. I am a cynical asshole, but IT security efforts are an exercise in hedging profits against legal exposure.
Let’s look at some facts that make it painfully obvious, organisations and their CISO’s are in the business of being “compliant” and not in securing your data.
Consequences
In their ASD Cyber Threat Report 2022-2023, the Australian Signals Directorate states that “ASD responded to over 1,100 cyber security incidents from Australian entities. Separately, nearly 94,000 reports were made to law enforcement through ReportCyber – around one every 6 minutes.”
That’s 3 reportable incidents a day. Which doesn’t account for the many that were not reported. The reporting scheme is voluntary and CISO’s are not reporting a breach unless they absolutely have too. Unnecessary reporting is a really fast way to become unemployed.
Now consider the consequences for those 1100 breaches.
- How many companies were fined and / or financially penalised for a data breach?
- 3, for a total of $6,154.37
- How many C level staff received a penalty or were fired for their involvement in a breach?
- None
- How many companies announced they have fired their CISO for a data breach?
- None
Some noteworthy cases investigated by the OAIC
- Marriott International got breached in that timeline and lost 2.2 million Australians details
- No penalty
- Datateks Pty Ltd was found to keep customer data in its sent items mailbox. This includes personal data, CC details, Drivers licences etc. The mailbox password was “Password1” [1]
- No penalty
- Pacific Lutheran College, determining that 367 individuals (affected individuals) were likely at risk of serious harm
- No penalty
Authority
Here’s the second piece of the puzzle. CISO’s have no authority to mandate, dictate or otherwise overrule the CEO or board. Or anyone else in the company unless the CEO says so.
Marketing could request the entire customer database be exported to a public Google Sheet, and the CISO couldn’t stop it if the CEO approves it. They can advise that it’s a terrible idea, they can point out the legislation or contracts it would breach, but they can’t say no.
In practice, what this means is that profitability always gets the green light at the expense of security. This applies from the small things like patching/upgrades right up to major business initiatives. Profits, trump security.
The most recent example of this is the Facebook court documents released in legal proceedings. Facebook has been caught implementing a man in the middle attack on Snapchat by using a VPN service. This is a blatant breach of customer security and would make any cybersecurity professional throw up.
At the time of the implementation, the Head of Security Engineering Pedro Canahuati, raised the following concern directly with Mark Zuckerberg (CEO)
I can’t think of a good argument for why this is okay. No security person is ever comfortable with this, no matter what consent we get from the general public. The general public just doesn’t know how this stuff works,
Pedro Canahuati
Zuckerberg simply overruled him and the project was implemented.
Canahuati had no authority to prevent the CEO taking action they knew would be unethical and legally dubious at best. While it’s true, he did get neutered, Canahuati could have had some integrity and resigned. Integrity tends to be in short supply at the C level, though.
On a side note, there is considerable irony that he is now the CTO at Password1. I wonder if he would look the other way if Jeff Shiner (CEO) asked him to allow a similar breach in the password managers software?
So what does a CISO do, if not secure systems?
Without the authority to control security within an organisation, all a CISO can do is try to minimise the damage to a breach and make sure that the company lawyers have something to work with in court.
CISO’s mitigate, by finding the absolute bare minimum that can be done to meet compliance, and then make sure everyone knows what risks are being signed off on. A smart CISO also keeps their receipts. Because when things go bad, the CEO is going to try to make sure they aren’t holding the shitty end of the stick.
Here’s a cheat sheet on how to fill the CISO role, while keeping your job and making sure you don’t get held accountable for the clusterfuck.
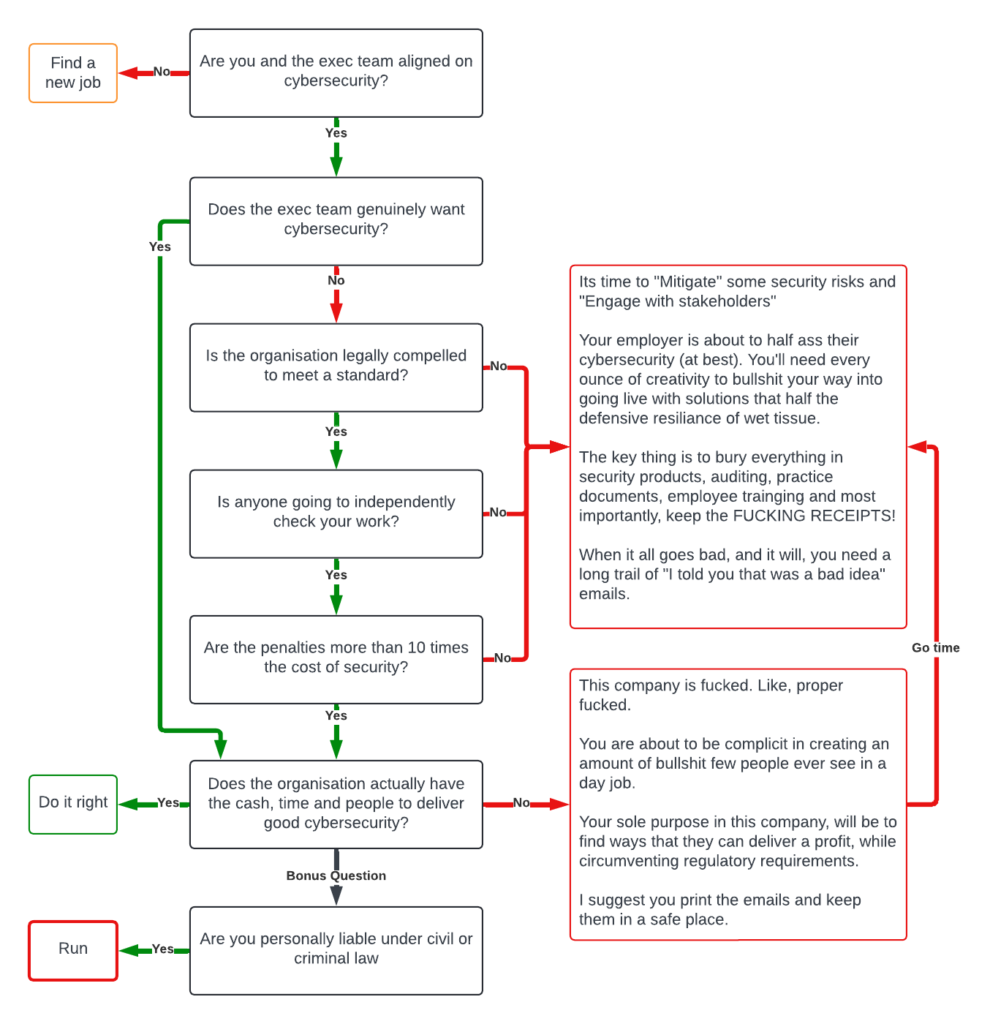
So next time you read about a data breach and are wondering how it happened, even with a cybersecurity team and CISO, the answer is simple.
Nobody was actually trying to keep the data safe. They were trying to keep the company profitable.